Thebigbop specializes in collecting useful exam dump content, we insist on year-round updates please follow us.
The latest Cisco CCDA 200-310 Exam questions and Answers, download the 200-310 PDF online and actually effectively
share it for free. You can practice testing 200-310 exam dumps online and improve your skills. All collections come from Pass4itsure.
Want to pass the 200-310 exam easily: https://www.pass4itsure.com/200-310.html (Q&As:600 Latest Update)
[PDF] Free Cisco CCDA 200-310 dumps download from Google Drive: https://drive.google.com/open?id=1TS0OYhsFtDLmVqUMhJaJ7Ja_SfDPB1h9
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1dq6fv9FX6zSDDoHc3ge-WzVU9SNaUbsH
200-310 desgn – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/200-310-desgn.html
Pass4itsure offers the latest Cisco CCDA 200-310 practice test free of charge (55Q&As)
QUESTION 1
DRAG DROP
Explanation
Explanation/Reference:
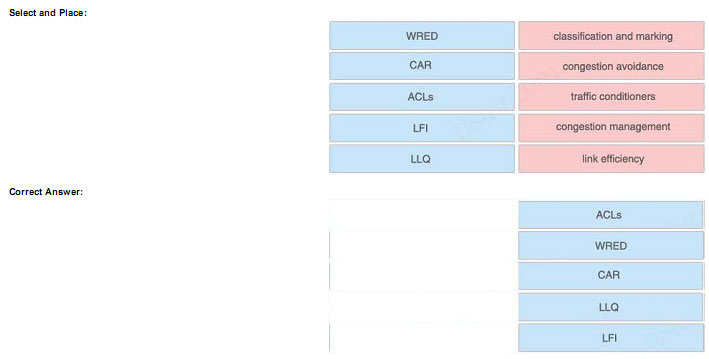
Classification is the process of partitioning traffic into multiple priority levels or classes of service. Information in the frame or packet header is
inspected, and the frame’s priority is determined. Marking is the process of changing the priority or class of service (CoS) setting within a frame or
packet to indicate its classification. Classification is usually performed with access control lists (ACL), QoS class maps, or route maps, using various
match criteria.
Congestion-avoidance techniques monitor network traffic loads so that congestion can be anticipated and avoided before it becomes problematic.
Congestion-avoidance techniques allow packets from streams identified as being eligible for early discard (those with lower priority) to be dropped when
the queue is getting full. Congestion avoidance techniques provide preferential treatment for high priority traffic under congestion situations while
maximizing network throughput and capacity utilization and minimizing packet loss and delay.
Weighted random early detection (WRED) is the Cisco implementation of the random early detection (RED) mechanism. WRED extends RED by
using the IP Precedence bits in the IP packet header to determine which traffic should be dropped; the drop-selection process is weighted by the IP
precedence.
Traffic conditioner consists of policing and shaping. Policing either discards the packet or modifies some aspect of it, such as its IP Precedence or
CoS bits, when the policing agent determines that the packet meets a given criterion. In comparison, traffic shaping attempts to adjust the transmission
rate of packets that match a certain criterion. Shaper typically delays excess traffic by using a buffer or queuing mechanism to hold packets and shape
the flow when the source’s data rate is higher than expected. For example, generic traffic shaping uses a weighted fair queue to delay packets to shape
the flow. Traffic conditioner is also referred to as Committed Access Rate (CAR).
Congestion management includes two separate processes: queuing, which separates traffic into various queues or buffers, and scheduling, which
decides from which queue traffic is to be sent next. There are two types of queues: the hardware queue (also called the transmit queue or TxQ) and
software queues. Software queues schedule packets into the hardware queue based on the QoS requirements and include the following types:
weighted fair queuing (WFQ), priority queuing (PQ), custom queuing (CQ), class-based WFQ (CBWFQ), and low latency queuing (LLQ).
LLQ is also known as Priority Queuing–Class-Based Weighted Fair Queuing (PQ-CBWFQ). LLQ provides a single priority but it’s preferred for VoIP
networks because it can also configure guaranteed bandwidth for different classes of traffic queue. For example, all voice call traffic would be assigned
to the priority queue, VoIP signaling and video would be assigned to a traffic class, FTP traffic would be assigned to a low-priority traffic class, and all
other traffic would
be assigned to a regular class.
Link efficiency techniques, including link fragmentation and interleaving (LFI) and compression. LFI prevents small voice packets from being
queued behind large data packets, which could lead to unacceptable delays on low-speed links. With LFI, the voice gateway fragments large packets
into smaller equal-sized frames and interleaves them with small voice packets so that a voice packet does not have to wait until the entire large data
packet is sent. LFI reduces and ensures a more predictable voice delay.
QUESTION 2
DRAG DROP
Explanation
Explanation/Reference:
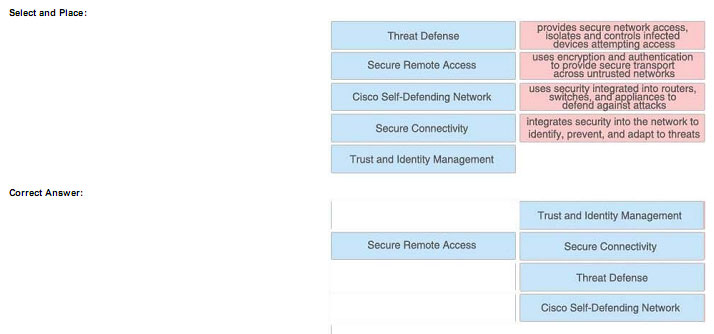
Trust and identity management solutions provide secure network access and admission at any point in the network and isolate and control infected or
unpatched devices that attempt to access the network. If you are trusted, you are granted access.
We can understand “trust” is the security policy applied on two or more network entities and allows them to communicate or not in a specific
circumstance. “Identity” is the “who” of a trust relationship.
The main purpose of Secure Connectivity is to protect the integrity and privacy of the information and it is mostly done by encryption and
authentication. The purpose of encryption is to guarantee confidentiality; only authorized entities can encrypt and decrypt data. Authentication is used to
establish the subject’s identity. For example, the users are required to provide username and password to access a resource…
QUESTION 3
DRAG DROP


Explanation
Explanation/Reference:
QUESTION 4
DRAG and DROP
 Explanation
Explanation
Explanation/Reference:
QUESTION 5
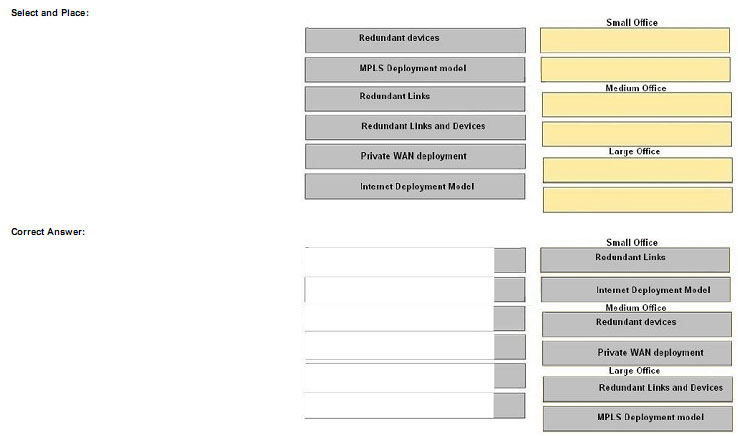
Drag the WAN characteristics on the left to the branch office model where it would most likely to be used on the right.
Explanation
Explanation/Reference:
QUESTION 6
The first phase of PPDIOO entails identifying customer requirements.
Drag the example on the left to the associated requirement on the right.

Explanation
Explanation/Reference:
QUESTION 7
Drag the description or characteristic on the left to the appropriate technology or protocol on the right.
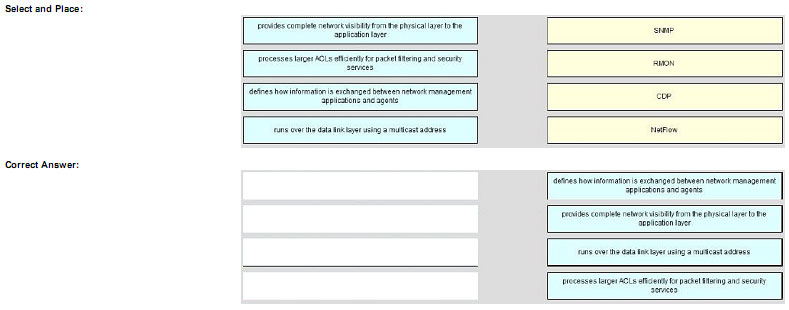
Explanation
Explanation/Reference:
QUESTION 8
Click and drag the phases of the PPDIOO network lifecycle approach on the left to their order on the right.
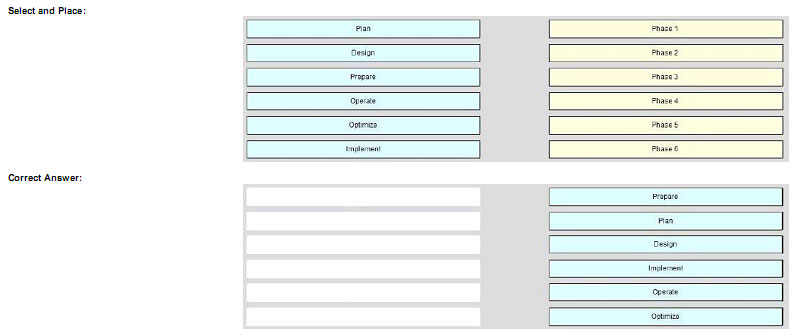
Explanation
Explanation/Reference:
QUESTION 9
Drag the characteristics of the traditional campus network on the left to the most appropriate hierarchical network layer on the right.
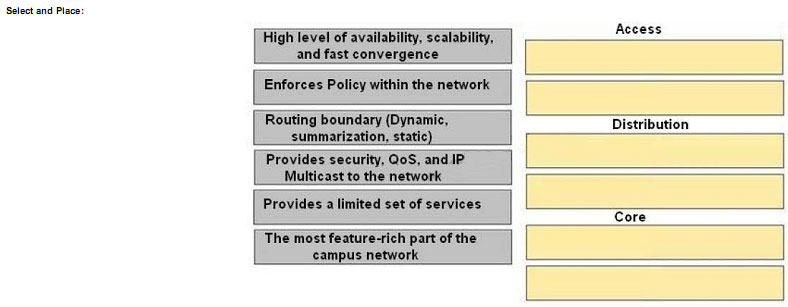

Explanation
Explanation/Reference:
QUESTION 10
Drag the network function on the left to the functional area or module where it is most likely to be performed in the enterprise campus infrastructure on the right.
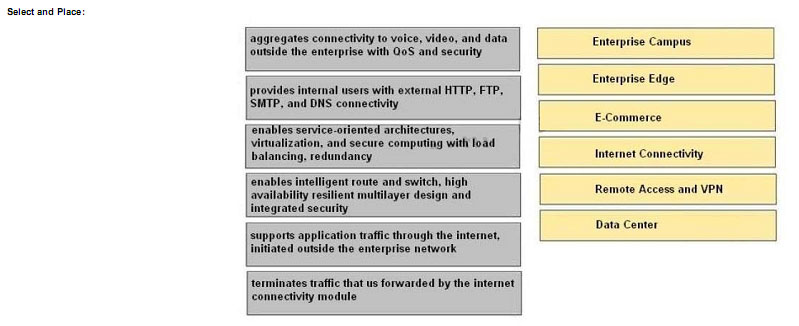
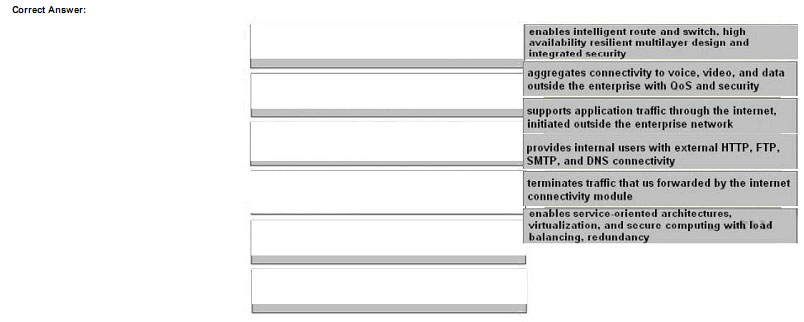
Explanation
Explanation/Reference:
QUESTION 11
Drag the security prevision on the left to the appropriate Network module on the right
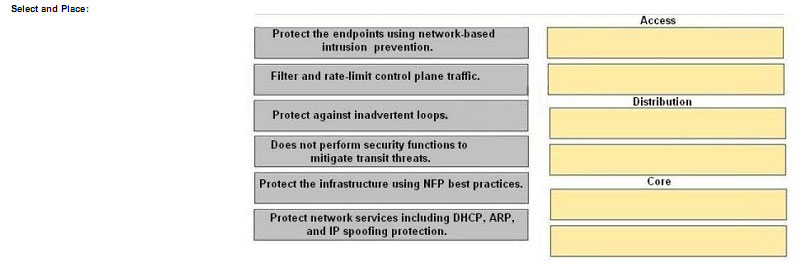
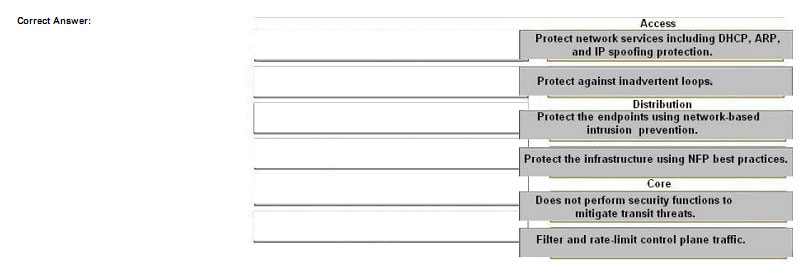
Explanation
Explanation/Reference:
QUESTION 12
Drag the technology on the left to the type of enterprise virtualization where it is most likely to be found on the right
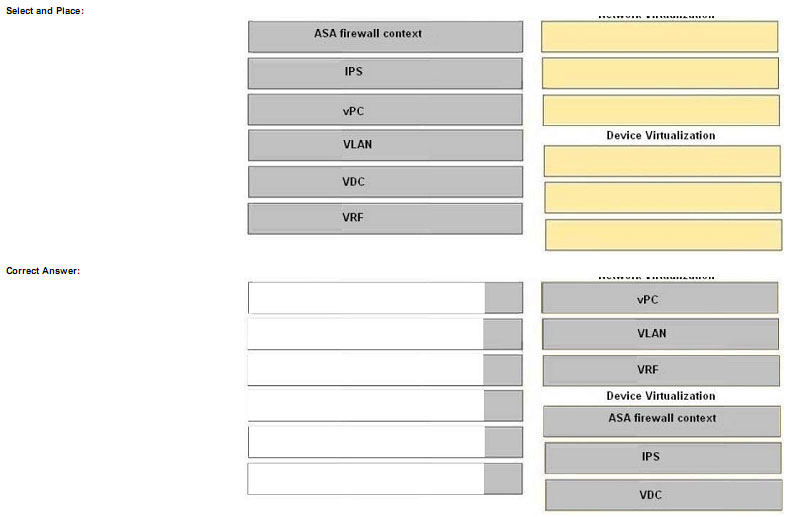
Explanation
Explanation/Reference:
QUESTION 13
Drag the network characteristic on the left to the design method on the right which will best ensure redundancy at the building distribution layer.
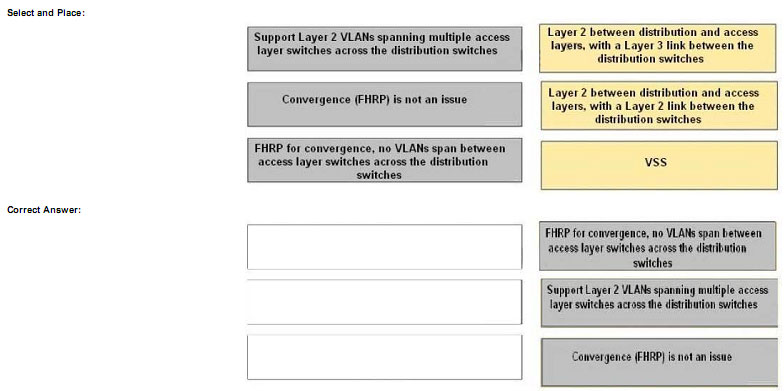
Explanation
Explanation/Reference:
QUESTION 14
Drag the associated virtualization tool or solution on the left to the appropriate design requirement on the right.

Explanation
Explanation/Reference:
QUESTION 15
Drag the WAN technology on the left to the most appropriate category on the right.
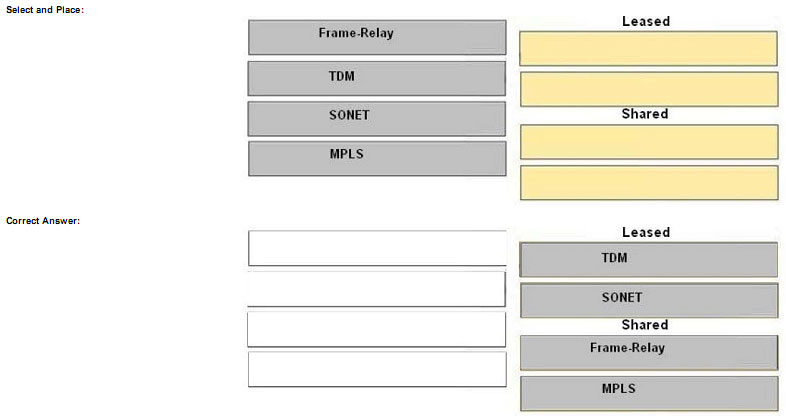
Explanation
Explanation/Reference:
QUESTION 16
Drag the STP toolkit term on the left to the definition on the right.
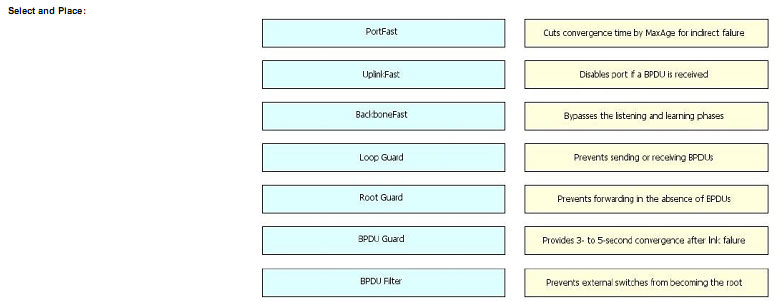

Explanation
Explanation/Reference:
QUESTION 17
Drag the characteristic on the left to the correct campus design model on the right
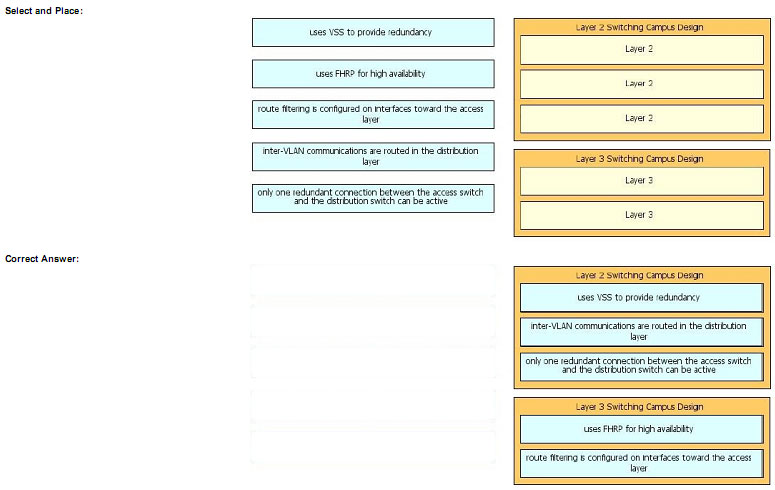
Explanation
Explanation/Reference:
QUESTION 18
Drag the technology on the left to the matching routing protocol on the right.
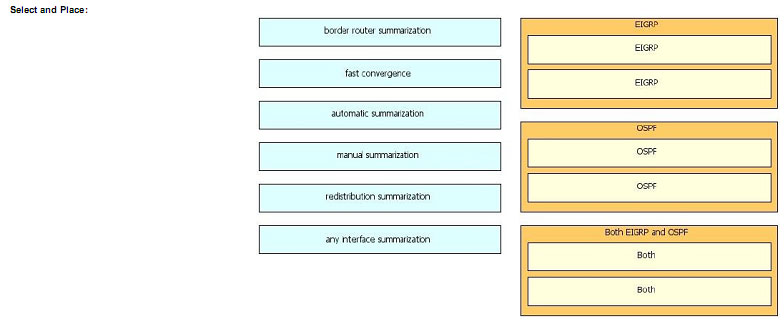
Explanation
Explanation/Reference:
QUESTION 19
Drag the security term on the left to the matching description on the right.
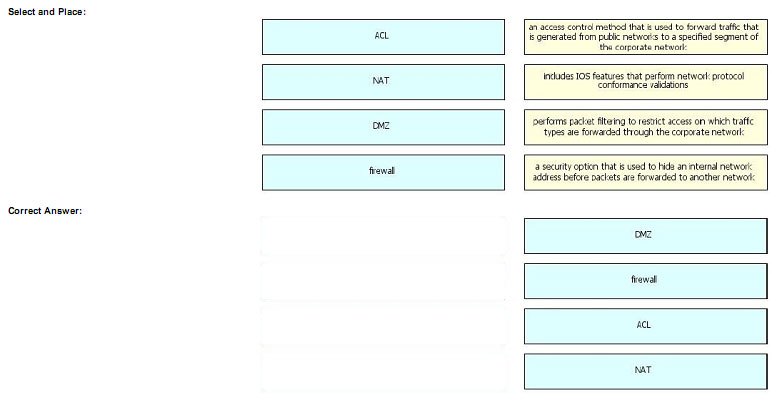
Explanation
Explanation/Reference:
QUESTION 20
Drag the term on the left to the matching deployment scenario on the right.
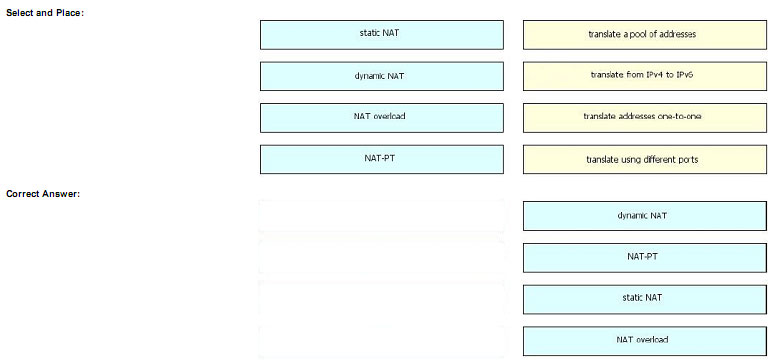
Explanation
Explanation/Reference:
QUESTION 21
Drag and drop the top-down approach process step 1 – 4 !
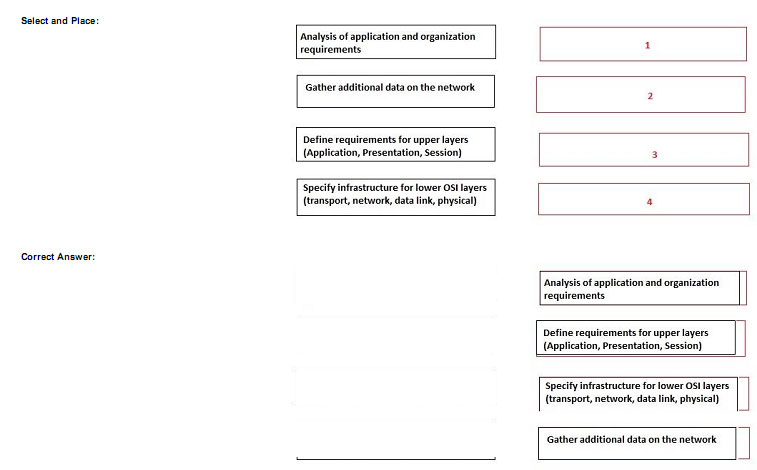
Explanation
Explanation/Reference:
QUESTION 22
DRAG DROP
Match the bandwidth usage optimization technique on the left with its definition on the right.
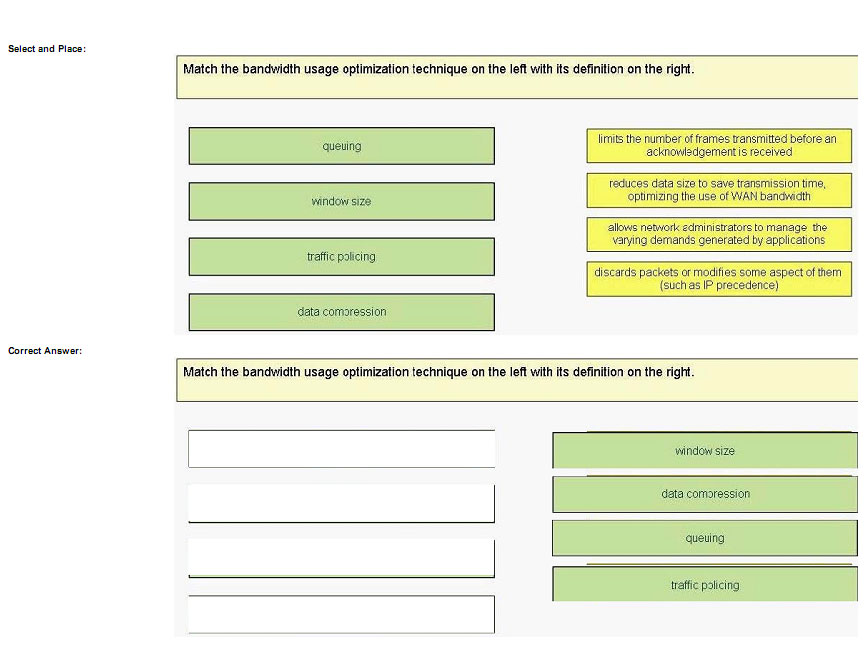
Explanation
Explanation/Reference:
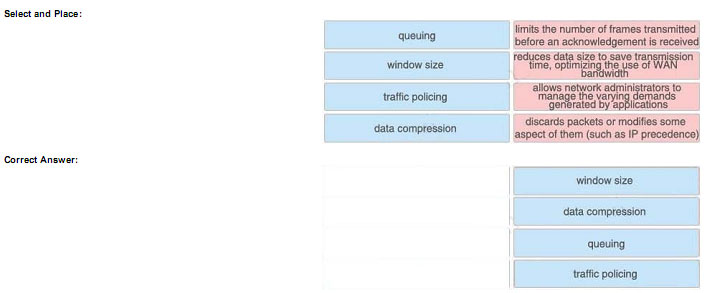
+ limits the number of frames transmitted before an acknowledgement is received: window size+ reduces data size to save transmission time, optimizing the use of WAN bandwidth: data compression+ allows network administrators to
manage the varying demands generated by applications: queuing+ discards packets or modifies some aspect of them (such as IP precedence): traffic policing
QUESTION 23
Which H.323 protocol monitors calls for factors such as packet counts, packet loss, and arrival jitter?
A. H.225
B. H.245
C. RAS
D. RTCP
Correct Answer: D
Explanation
QUESTION 24
When designing using the Cisco Enterprise Architecture, in which Enterprise Campus layer does the Enterprise Teleworker module establish its connection?
A. Building Core
B. Building Access
C. Enterprise Branch
D. Enterprise Data CenterE. WAN/Internet
Correct Answer: E
Explanation
QUESTION 25
The BodMech online fitness organization specializes in creating fitness plans for senior citizens. The company recently added a health-products retail inventory. Which E-Commerce module device will allow customers to interact with the
company and purchase products?
A. application server
B. database server
C. public server
D. web server
E. NIDS appliance
F. SMTP mail server
Correct Answer: D
Explanation
QUESTION 26
Which two wireless attributes should be considered during a wireless site survey procedure? (Choose two.)
A. encryption
B. channel
C. authentication
D. power
E. SSID
Correct Answer: BD
Explanation
QUESTION 27
You are performing an audit of a customer’s existing network and need to obtain the following router information:
Interfaces
running processes
IOS image being executed
Which command should you use?
A. show version
B. show tech-support
C. show startup-config
D. show running-config
E. show processes memory
Correct Answer: B
Explanation
QUESTION 28
Which of these domain-of-trust security statements is correct?
A. Segments within a network should have the same trust models.
B. An administrator should apply consistent security controls between segments.
C. Communication between trusted entities needs to be carefully managed and controlled.
D. Segment security policy decisions are based on trust.
Correct Answer: D
Explanation
QUESTION 29
When collecting information about a customer’s existing network, which two sources will provide the most accurate data? (Choose two.)
A. traffic analysis
B. customer interview
C. customer-supplied server list
D. existing network topology diagram
E. configurations obtained from network equipment
Correct Answer: AE
Explanation
QUESTION 30
Which modules are found in the Enterprise Edge functional area of the Cisco Enterprise Architecture? Select all that apply.
A. Teleworker
B. WAN/MAN
C. Server Farm
D. E-Commerce
E. Internet Connectivity
F. Remote Access/VPN
Correct Answer: BDEF
Explanation
QUESTION 31
Which H.323 protocol is responsible for the exchanging of capabilities and the opening and closing of logical channels?
A. H.225
B. H.245
C. RAS
D. RTCP
Correct Answer: B
Explanation
QUESTION 32
Which one of the following represent correct IPv6 Global Unicast address format?
A. 48bit(Global Prefix)+16bit(Subnet ID)+64bit(Interface ID)
B. 16bit(Subnet ID)+ 48bit(Global Prefix)+64bit(Interface ID)
C. 64bit(Interface ID)+16bit(Subnet ID)+ 48bit(Global Prefix)
D. 64bit(Interface ID)+ 48bit(Global Prefix)+16bit(Subnet ID)
Correct Answer: A
Explanation
QUESTION 33
What is the maximum number of switches in VSS?
A.2B. 4
C. 6
D. 8
Correct Answer: A
Explanation
QUESTION 34
What DNS entry to use for WLC with firmware version 6.0 or later so an Access Point can determine the controller’s IP address?
A. DNS A record with controller’s hostname
B. DHCP option 43
C. cisco-capwap-controller
D. cisco-lwapp-controller
Correct Answer: C
Explanation
QUESTION 35
Two companies that want to connect with multiple providers vendors, what protocol is the proper one to use?
A. BGP
B. IS-IS
C. OSPF
D. EIGRP
Correct Answer: A
Explanation
QUESTION 36
Which subnet mask should you use on point-to-point links to avoid wasting IP addresses?
A. 255.255.255.252
B. 255.255.255.250
C. 255.255.255.0
D. 255.255.255.248
Correct Answer: A
Explanation
QUESTION 37
Which virtualization deployment an engineer will execute to separate to accomplish security policies?
A. Same corporate Network with NAC capabilities.
B. Something using VLANs
Correct Answer: B
Explanation
QUESTION 38
What statement about EVN is true?
A. Support RIP
B. Support OSPFV3
C. Required LDP
D. Support as many as 32 virtual networks per device
Correct Answer: D
Explanation
QUESTION 39
Consider the reservation of IP Addressing what mask you will use in a point to point connection between two Buildings?
A. 255.255.252.0
B. 255.255.255.252
C. 255.255.255.254
Correct Answer: B
Explanation
QUESTION 40
What describes the link performance?
A. Bandwidth
B. Utilization
C. Availability
Correct Answer: A
Explanation
Explanation/Reference:
Explanation: https://en.wikipedia.org/wiki/Network_performance
QUESTION 41
What tool would you use to capture, segregate and analyse IP traffic?
A. Protocol Analyser
B. NetFlow
Correct Answer: B
Explanation
QUESTION 42
What tool would you use to decode protocols?
A. Protocol Analyser
B. NetFlow
C. Spectrum Analyser
Correct Answer: A
Explanation
QUESTION 43
What should be considered when scaling EIGRP? (Choose three)
A. CPU
B. Peers
C. Query scope
D. Interface Bandwidth
E. Memory
F. IP Address
Correct Answer: BCF
Explanation
Explanation/Reference:
Explanation: http://lostintransit.se/2013/11/23/eigrp-network-design/
QUESTION 44
Which two high-level design components are included in Unified Wireless network?
A. Local
B. Cisco FlexConnect
C. Deterministic
D. N+1
E. Dynamic
Correct Answer: AB
Explanation
QUESTION 45
How to reduce the size of a routing table? (Choose two):
A. NAT
B. Summarization
C. Static routes
D. VLAN
Correct Answer: AB
Explanation
QUESTION 46
What query should you make if you want to find all objects of a particular type in an MIT tree?
A. mid-tree-level
B. class-level
C. object-level
D. tree-level
Correct Answer: B
Explanation
QUESTION 47
What will extend a trust boundary (there is switch interface configuration with separate voice VLAN and data VLAN configured where the phone is connected to, also small diagram showing endpoint (host), IP Phone, Access Switch,
Distribution Switch, Core Switch and Data Centre Aggregation switch)?
A. Multiple layers PC
B. IP Phone
C. Access Switch
D. Distribution Switch
E. Core Switch
Correct Answer: D
Explanation
QUESTION 48
What kind of servers you should place in DMZ?
A. WWW
B. FTP
C. DHCP
D. TACACS+
E. NFP
Correct Answer: AB
Explanation
QUESTION 49
What access policies to set up for remote VPN access (Choose three)?
A. Admins are centrally authenticated with full network access
B. Partners are centrally authenticated with access limited by use of ACLs
C. Employees are centrally authenticated with access limited by use of ACLs
D. Admins are locally authenticated with full network access
E. Partners are centrally authenticated with full access
F. Employees are centrally authenticated with full access
Correct Answer: ABC
Explanation
QUESTION 50
An organization needs to implement isolated logical structure due to compliance regulations. What complex access control network virtualization method can it use?
A. The IT organization creates a quarantine network for end points that do not meet the posture assessment requirements
B. The IT organization creates a separate guest network for wireless and wired clients
C. The IT organization acts as a client serving different, isolated departments
Correct Answer: A
Explanation
QUESTION 51
What are two advantages of a modular design? (Choose two)
A. Increased scalability
B. Security can be implemented at every module
C. Increased redundancy as you can add modules
D. Hierarchy included in design
Correct Answer: AC
Explanation
Explanation/Reference:
References:
http://www.ciscopress.com/articles/article.asp?p=1073230&seqNum=2 https://thwack.solarwinds.com/docs/DOC-175763
QUESTION 52
What is the best point to deploy the IPS, not to have false positives, since the traffic is already filtered?
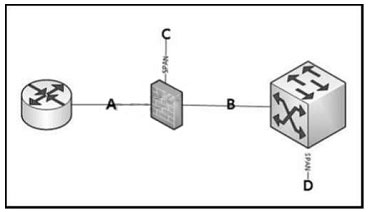
A. Inline before the firewallB. Inline after the firewall
C. Passive of the firewall
D. Passive of the Switch
Correct Answer: D
Explanation
Explanation/Reference:
Reference:
https://supportforums.cisco.com/t5/intrusion-prevention-systems-ids/correct- placement-of-ids-ips-in-network-architecture/td-p/2632437
QUESTION 53
What VPN tunneling technology supports multicast?
A. DMVPN spoke-to-spoke
B. IPSec direct tunnelling hub-and-spoke
C. Easy VPN
D. IPSec direct tunnelling spoke-to-spoke
Correct Answer: A
Explanation
QUESTION 54
Which one of the following is “synchronous link” design?
A. SSL VPN over serial cable modem
B. Bonded T1s
C. Internet VPN
D. MPLS VPN
Correct Answer: B
Explanation
QUESTION 55
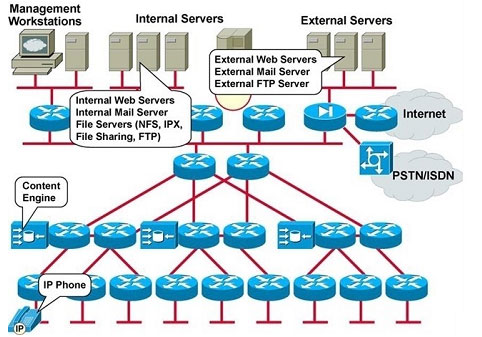
Refer to the exhibit. Which element or elements of the existing network infrastructure does this network map emphasize?
A. network services
B. network protocols
C. the OSI data link layer
D. network applications
Correct Answer: D
Explanation
Conclusion:
Thanks for reading, improving Cisco CCDA 200-310 Exam skills is very meaningful, we offer 55 valid Cisco 200-310 exam dumps and 200-310 PDF downloads free of charge. Free content can enhance your skills to help you open the door to learning. If you want to get 200-310 Exam certification: https://www.pass4itsure.com/200-310.html (q&as:600 ).Guaranteed to pass easily.
[PDF] Free Cisco CCDA 200-310 dumps download from Google Drive: https://drive.google.com/open?id=1TS0OYhsFtDLmVqUMhJaJ7Ja_SfDPB1h9
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1dq6fv9FX6zSDDoHc3ge-WzVU9SNaUbsH
pass4itsure 15% OFF Coupon code
related: https://www.exametc.net/100-pass-rate-microsoft-62-193-dumps/
