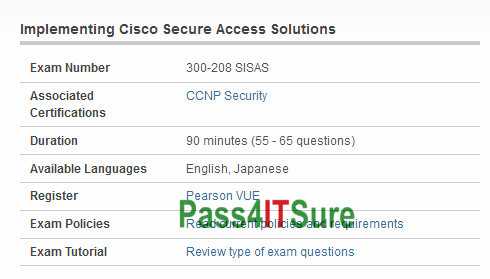
Have you wandered why other IT people can easily pass new Cisco 300-208 dumps exam simulator test? The Implementing Cisco Secure Access Solutions (300-208 SISAS) exam is a 90 minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCNP Security certification. Valid and updated Cisco SISAS 300-208 dumps practice test certification CCNP Security exam video training online. “Implementing Cisco Secure Access Solutions” is the exam name of Pass4itsure Cisco 300-208 dumps test which designed to help candidates prepare for and pass the Cisco 300-208 exam. The Implementing Cisco Secure Access Solutions (SISAS) (300-208) exam tests whether a network security engineer knows the components and architecture of secure access, by utilizing 802.1X and Cisco TrustSec. Candidates can prepare for this https://www.pass4itsure.com/300-208.html exam by taking the Implementing Cisco Secure Access Solutions (SISAS) course.
[Jan-2018-Cisco 300-208 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWd0NtZHRiUmJNV2s
[Jan-2018-Cisco 300-209 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWTlN6bWE4ckRMNmc
Welcome to Pass4itsures Blog: Free Cisco 300-208 Dumps(1-33)
QUESTION 1
You have configured a Cisco ISE 1.2 deployment for self-registration of guest users. What two options can you select from to determine when the account duration timer begins? (Choose two.)
A. CreateTime
B. FirstLogin
C. BeginLogin
D. StartTime
300-208 exam Correct Answer: AB
QUESTION 2
What is a feature of Cisco WLC and IPS synchronization?
A. Cisco WLC populates the ACLs to prevent repeat intruder attacks.
B. The IPS automatically send shuns to Cisco WLC for an active host block.
C. Cisco WLC and IPS synchronization enables faster wireless access.
D. IPS synchronization uses network access points to provide reliable monitoring.
Correct Answer: B
QUESTION 3
Which three network access devices allow for static security group tag assignment? (Choose three.)
A. intrusion prevention system
B. access layer switch
C. data center access switch
D. load balancer
E. VPN concentrator
F. wireless LAN controller
300-208 dumps Correct Answer: BCE
QUESTION 4
Which command in the My Devices Portal can restore a previously lost device to the network?
A. Reset
B. Found
C. Reinstate
D. Request
Correct Answer: C
QUESTION 5
Which CoA type does a Cisco ISE PSN send to a network access device when a NAG agent reports the OS patch status of a noncompliant endpoint?
A. CoA-Terminate
B. CoA-PortBounce
C. CoA-Reauth
D. CoA-Remediate
300-208 pdf Correct Answer: C
QUESTION 6
Which option is one method for transporting security group tags throughout the network?
A. by embedding the SGT in the IP header
B. via Security Group Exchange Protocol
C. by embedding the SGT in the 802.1Q header
D. by enabling 802.1AE on every network device
Correct Answer: B
QUESTION 7
Which two conditions are valid when configuring ISE for posturing? (Choose two.)
A. Dictionary
B. member Of
C. Profile status
D. File
E. Service
300-208 vce Correct Answer: DE
QUESTION 8
Which mechanism does Cisco ISE use to force a device off the network if it is reported lost or stolen?
A. CoA
B. dynamic ACLs
C. SGACL
D. certificate revocation
Correct Answer: A
QUESTION 9
Which three pieces of information can be found in an authentication detail report? (Choose three.)
A. DHCP vendor ID
B. user agent string
C. the authorization rule matched by the endpoint
D. the EAP method the endpoint is using
E. the RADIUS username being used
F. failed posture requirement
300-208 exam Correct Answer: CDE
QUESTION 10
Your guest-access wireless network is experiencing degraded performance and excessive latency due to user saturation. Which type of rate limiting can you implement on your network to correct the problem?
A. per-device
B. per-policy
C. per-access point
D. per-controller
E. per-application
Correct Answer: A
QUESTION 11
Which three host modes support MACsec? (Choose three.)
A. multidomain authentication host mode
B. multihost mode
C. multi-MAC host mode
D. single-host mode
E. dual-host mode
F. multi-auth host mode
300-208 dumps Correct Answer: ABD
QUESTION 12
An administrator can leverage which attribute to assign privileges based on Microsoft Active Directory user groups?
A. member of
B. group
C. class
D. person
Correct Answer: A
QUESTION 13
Within a BYOD environment, when employees add devices using the My Devices Portal, which Identity Group does Cisco ISE add the endpoints to?
A. Registered
B. Employee
C. Guest
D. Profiled
300-208 pdf Correct Answer: A
QUESTION 14
Which three events immediately occur when a user clicks andquot;Registerandquot; on their device in a single-SSID BYOD onboarding registration process (Choose three).
A. CA certificate is sent to the device from Cisco ISE
B. An endpoint is added to a RegistereDevices identity group
C. RADIUS access request is sent to Cisco ISE
D. The profile service is sent to the device from Cisco ISE
E. dACL is sent to the device from Cisco ISE
F. BYOD registration flag is set by Cisco ISE
Correct Answer: ABF
QUESTION 15
How many bits are in a security group tag?
A. 64
B. 8
C. 16
D. 32
300-208 vce Correct Answer: C
QUESTION 16
Which two Active Directory authentication methods are supported by Cisco ISE? (Choose two.)
A. MS-CHAPv2
B. PEAP
C. PPTP
D. EAP-PEAP
E. PPP
Correct Answer: AB
QUESTION 17
Which network component would issue the CoA?
A. switch
B. endpoint
C. Admin Node
D. Policy Service Node
300-208 exam Correct Answer: D
QUESTION 18
When you select Centralized Web Auth in the ISE Authorization Profile, which component hosts the web authentication portal?
A. the endpoints
B. the WLC
C. the access point
D. the switch
E. ISE
Correct Answer: E
QUESTION 19
A malicious user gained network access by spoofing printer connections that were authorized using MAB on four different switch ports at the same time. What two catalyst switch security features will prevent further violations? (Choose two)
A. DHCP Snooping
B. 802.1AE MacSec
C. Port security
D. IP Device tracking
E. Dynamic ARP inspection
F. Private VLANs
300-208 dumps Correct Answer: AE
QUESTION 20
A network administrator is seeing a posture status andquot;unknownandquot; for a single corporate machine on the Cisco ISE authentication report, whereas the other machines are reported as andquot;compliantandquot;. Which option is the reason for machine being reported as andquot;unknownandquot;?
A. Posture agent is not installed on the machine.
B. Posture policy does not support the OS.
C. Posfure compliance condition is missing on the machine.
D. Posture service is disabled on Cisco ISE.
Correct Answer: A
QUESTION 21
Which option describes the purpose of configuring Native Supplicant Profile on the Cisco ISE?
A. It helps employees add and manage new devices by entering the MAC address for the device.
B. It is used to register personal devices on the network.
C. It enforces the use of MSCHAPv2 or EAP-TLS for 802.1X authentication.
D. It provides posture assessments and remediation for devices that are attempting to gain access to the corporate network.
300-208 pdf Correct Answer: C
QUESTION 22
During client provisioning on a Mac OS X system, the client system fails to renew its IP address. Which change can you make to the agent profile to correct the problem?
A. Enable the Agent IP Refresh feature.
B. Enable the Enable VLAN Detect Without UI feature.
C. Enable CRL checking.
D. Edit the Discovery Host parameter to use an IP address instead of an FQDN.
Correct Answer: A
QUESTION 23
You are installing Cisco ISE on nodes that will be used in a distributed deployment. After the initial bootstrap process, what state will the Cisco ISE nodes be in?
A. Remote
B. Policy service
C. Administration
D. Standalone
300-208 vce Correct Answer: D
QUESTION 24
What implementation must be added to the WLC to enable 802.1X and CoA for wireless endpoints?
A. the ISE
B. an ACL
C. a router
D. a policy server
Correct Answer: A
QUESTION 25
You have configured a Cisco ISE1.2 deployment for self registration of guest users. What two options can you select from to determine when the account duration timer begins(Choose two)?
A. Createtime
B. Firstlogin
C. Approvaltime
D. Custom
E. Starttime
300-208 exam Correct Answer: AB
QUESTION 26
Which three algorithms should be avoided due to security concerns? (Choose three.)
A. DES for encryption
B. SHA-1 for hashing
C. 1024-bit RSA
D. AES GCM mode for encryption
E. HMAC-SHA-1
F. 256-bit Elliptic Curve Diffie-Hellman
G. 2048-bit Diffie-Hellman
Correct Answer: ABC
QUESTION 27
Which debug command on a Cisco WLC shows the reason that a client session was terminated?
A. debug dot11 state enable
B. debug dot1x packet enable
C. debug client mac addr
D. debug dtls event enable
E. debug ap enable cisco ap
300-208 dumps Correct Answer: C
QUESTION 28
How frequently does the Profiled Endpoints dashlet refresh data?
A. every 30 seconds
B. every 60 seconds
C. every 2 minutes
D. every 5 minutes
Correct Answer: B
QUESTION 29
Which two profile attributes can be collected by a Cisco Wireless LAN Controller that supports Device Sensor? (Choose two.)
A. LLDP agent information
B. user agent
C. DHCP options
D. open ports
E. CDP agent information
F. FQDN
300-208 pdf Correct Answer: BC
QUESTION 30
Which five portals are provided by PSN? (Choose five.)
A. guest
B. sponsor
C. my devices
D. blacklist
E. client provisioning
F. admin
G. monitoring and troubleshooting
Correct Answer: ABCDE
QUESTION 31
An auditor for a major retail company suspects that inventory fraud is occurring at three stores which have high costs of goods sold. Which of the following audit activities would provide the most persuasive evidence that fraud is occurring?
A. Use an integrated test facility (ITF) to compare individual sales transactions with test transactions submitted through the ITF and investigate all differences.
B. Interview the three individual store managers to determine if their explanations about the observed differences are the same, and then compare their explanations to that of the section manager.
C. Schedule a surprise inventory audit to include a physical inventory and investigate areas of inventory shrinkage.
D. Select a sample of individual store prices and compare them with the sales entered on the cash register for the same items.
300-208 vce Correct Answer: C
QUESTION 32
Which of the following procedures would be most helpful in providing additional evidence when an auditor suspects that an unidentified employee is submitting and approving invoices for payment?
A. Use generalized audit software to identify invoices from vendors with post office box numbers or other unusual features. Select a sample of those invoices and trace to supporting documents such as receiving reports.
B. Select a sample of payments made during the year and investigate each one for approval.
C. Select a sample of receiving reports representative of the period under investigation and trace to approved payment. Note any items not properly processed.
D. Select a sample of invoices paid during the past month and trace them to appropriate vendor accounts.
Correct Answer: A
QUESTION 33
Insurance companies often receive electronic hospitalization claims directly from hospitals. Which of the following control procedures would be most effective in detecting fraud in such an environment?
A. Use integrated test facilities to test the accuracy of processing in a manner that is transparent to data processing.
B. Develop monitoring programs to identify unusual types of claims or an unusual number of claims by demographic class for investigation by the claims department.
C. Use generalized audit software to match the claimant identification number with a master list of valid policyholders.
D. Develop batch controls over all items received from a particular hospital and process those claims in batches.
300-208 exam Correct Answer: B

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products. Our Cisco 300-208 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
This 90-minute 300-208 dumps exam consists of 65-75 questions and assesses knowledge of Cisco Identity Services Engine (ISE) architecture, solution, and components as an overall network threat mitigation and endpoint control solutions. It also includes the fundamental concepts of bring your own device (BYOD) using posture and profiling services of ISE. “Implementing Cisco Secure Access Solutions”, also known as 300-208 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 300-208 dumps exam questions answers are updated (282 Q&As) are verified by experts. The associated certifications of https://www.pass4itsure.com/300-208.html dumps is CCNP Security.
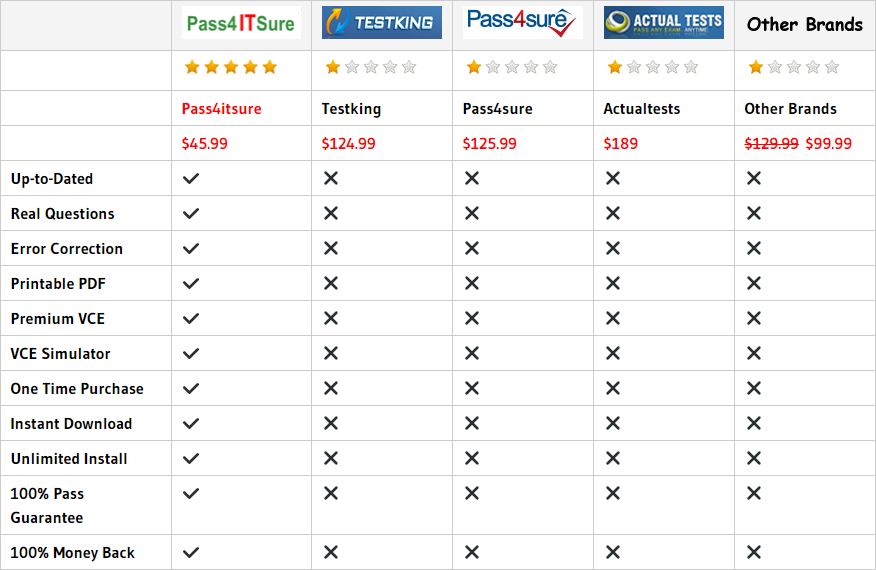
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure Cisco 300-208 Dumps Tests, Valid and updated Cisco 300-208 Dumps Certification Exam Online Shop,We Help You Pass Implementing Cisco Secure Access Solutions. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!
